Cyber Security
VAPT Services – To make tomorrow better, today.
Vulnerability assessment is the process of identifying and prioritizing security issues pertaining to Network, Web Applications, Mobile Applications for your organization. VAPT is a mechanism to check the effectiveness of controls on your Network, Web Application and Mobile Apps. Based on the scope the organization provides for scan, we will be evaluating using established vulnerability scanning techniques.
Network Penetration testing is of two types:
- External Network VAPT
- Internal Network VAPT.
External Network VAPT targets scanning of external facing network resources to assess the defensive capabilities of your organization external network. Internal Network VAPT is done to evaluate the internal security controls and provide recommendation for its improvement. It also helps in improving the compliance and overall security posture of your organization.
Services
Our experts at your service for Cloud ComputingWith rise in Digitalization across enterprise many applications are exposed to external access and this has increased the attack surface for application exploitation. Our experts will evaluate the security posture of the applications by simulating real life attack scenarios. This helps in identifying the application security weakness which could be exploited by potential attackers to help organizations close the security flaws in their environment.
We highly recommend enterprises to do this assessment twice in a year by continuously evaluating the environment or as per the regulatory mandate.
UKBIT approach to cybersecurity includes having a current, intimate knowledge of enterprise assets, while regularly undertaking assessments of network perimeter, applications, data, infrastructure, threat modelling and internal systems. These include independent assurance tests that take place annually, or after significant changes to infrastructure, applications, processes or personnel.
Data Protection & Privacy
Data security and privacy risks are becoming more prominent for both small, medium and large organizations today. Businesses across the globe are facing productivity loss and are running at higher data security risk. Current data protection methods are rendered obsolete due to incessant growth in data generation and usage across multiple data silos/ streams in an organization. UKBIT data-centric protection and privacy service offers holistic technology solution to secure sensitive data in your organization across creation, use and transmission. It incorporates a risk-based strategy with leading data protection solutions to protect your organization’s critical data across its lifecycle.
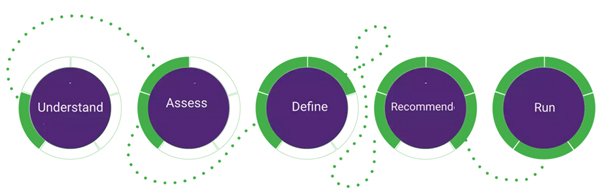
UKBIT Data Protection & Privacy Services
Using 5 stage transformational approach.
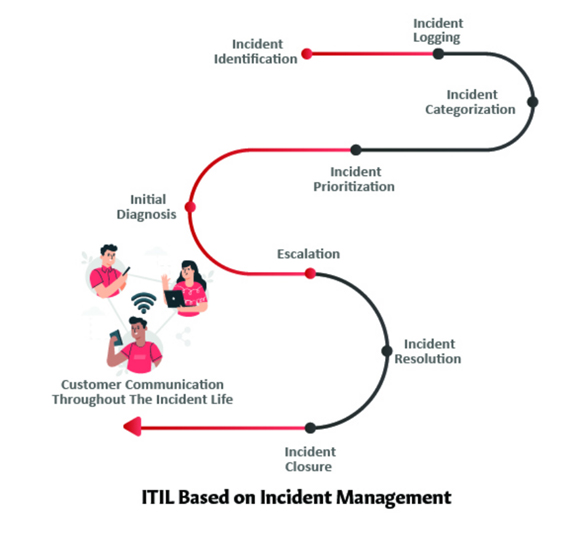
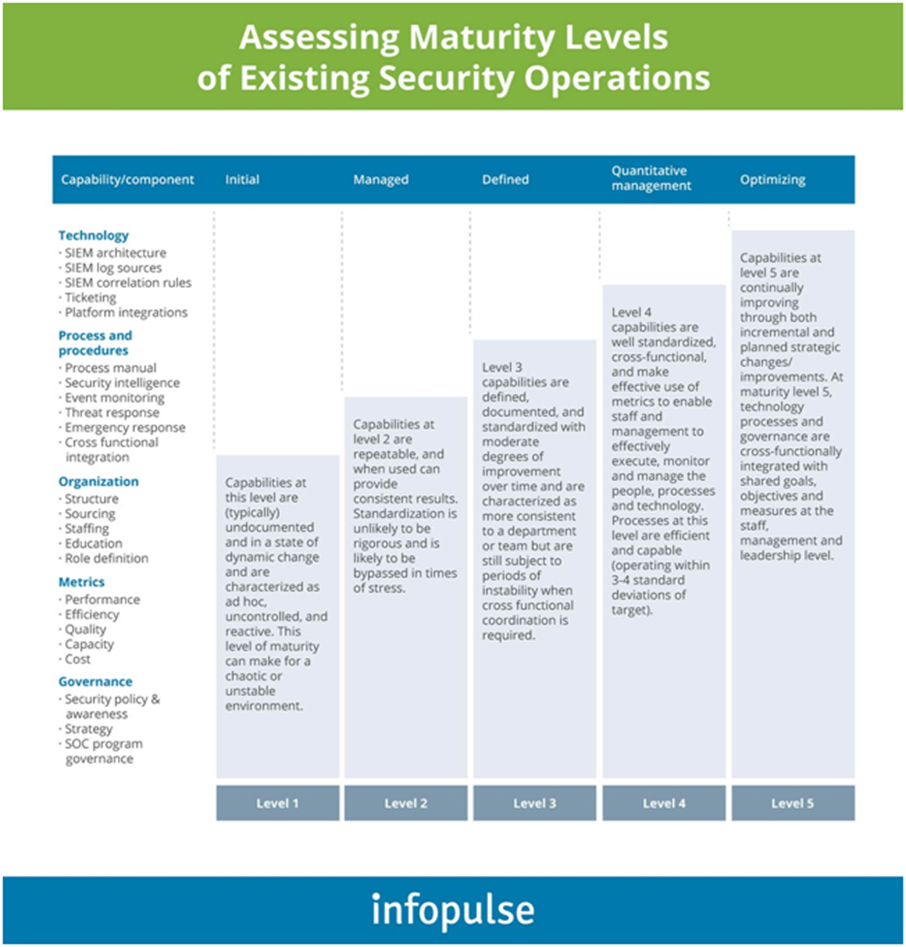
What is a Security Operations Center?
A Security Operations Center operates in many ways that are analogous to the human immune system, which actively monitors, hunts, recognizes, alerts, and prevents/neutralizes real-time cyber-threats. This requires a team of dedicated security analysts with access to the latest threat intelligence and knowledge of the evolving security threat landscape. SOC typically uses event ingestion and analysis tool called SIEM (Security Information and Event Management) that collects a voluminous amount of security events, logs, packets from systems across the enterprise. This allows analysts to correlate events, hunt malicious or suspicious access patterns, and identify threats based on active threat intelligence. Analysts may also handle or suggest remediation such as patch application, configurations modification, and system upgrades.
Why SOC?
As almost all the organizations have started to adopt a remote-working strategy to cope with the pandemic situation, having cybersecurity solutions for remote working conditions is becoming mandatory. A recent cybersecurity report indicates that 31% of enterprises have experienced cyber-attacks on operational technology infrastructure. This also denotes that vulnerabilities are rising in number and broadening severities too. The result to reduce these intrusions leads enterprises to invest in a Security Operations Centre (SOC). The main objective of a SOC is to detect monitor, analyze and react to security incidents with the integration of futuristic tools, cutting-edge technologies, and a robust security strategy.